Ethereum: DDOS attack via BRC-20 & ordinals on Bitcoin
Ethereum: DDOS attack via BRC-20 and ordinals on Bitcoin?
Recently, there has been growing concern about the possibility of a distributed denial of service (DDoS) attack targeting the Ethereum network. However, what may seem like an unusual scenario is actually related to the use of certain cryptocurrency tokens and protocols: BRC-20 and serial numbers.
History of the BRC-20 issue and serial numbers
BRC-20 is a token based on the Ethereum blockchain. It is designed for micropayments, allowing users to send small amounts to each other without the need for intermediaries such as traditional payment systems. On the other hand, ordinals are an extension of BRC-20, allowing users to transfer and store tokens in a more secure and transparent way.
Problem: High Fees, Low Value Transactions
Despite being a low-cost transaction protocol, Ordinals generate significant amounts of fees due to their decentralized nature. This led to a situation where the mempool (transaction queue of the Ethereum network) is overflowing with transactions with small amounts, including BRC-20 and serial numbers.
DDoS Attack Scenario: Mempool Overflow
A potential DDoS attack could exploit this issue by flooding the Ethereum network with high-value transactions, causing congestion and slowing down the entire protocol. This will have significant consequences for users using the Ethereum network, as well as for the broader ecosystem of cryptocurrencies.
Is a real DDOS attack happening?
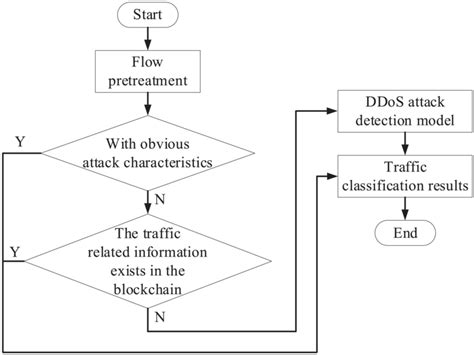
Unfortunately, yes. There are reports of DDoS attacks targeting Bitcoin mining nodes and pools, which could have cascading effects on the entire blockchain ecosystem. However, it is important to note that such attacks are usually aimed at specific nodes or pool operators, and not at the wider Ethereum network.
What can be done?
A number of measures can be taken to reduce this risk:
- Optimization of transaction fees
: increasing the efficiency of transactions and reducing unnecessary fees can help reduce congestion in the memory pool.
- Implementation of protection against DDoS attacks: Developing and deploying anti-DDoS software or solutions to detect and prevent attacks is critical to protecting the Ethereum network.
- Improving Node Security: Implementing robust node security measures, such as multi-factor authentication and secure communication protocols, can help protect nodes from DDoS attacks.
- Monitor and analyze traffic patterns: constant monitoring of transaction volumes, commissions and network load can provide valuable information about potential problems and allow you to develop proactive strategies to eliminate them.
Schlussfolgerung
Although there is currently no real DDO attack on Bitcoin, the problem of overfilling the memory pool with large transactions is a serious concern. By understanding the main factors contributing to this problem and implementing measures to mitigate it, we can work to create a safer and more sustainable cryptocurrency ecosystem.
